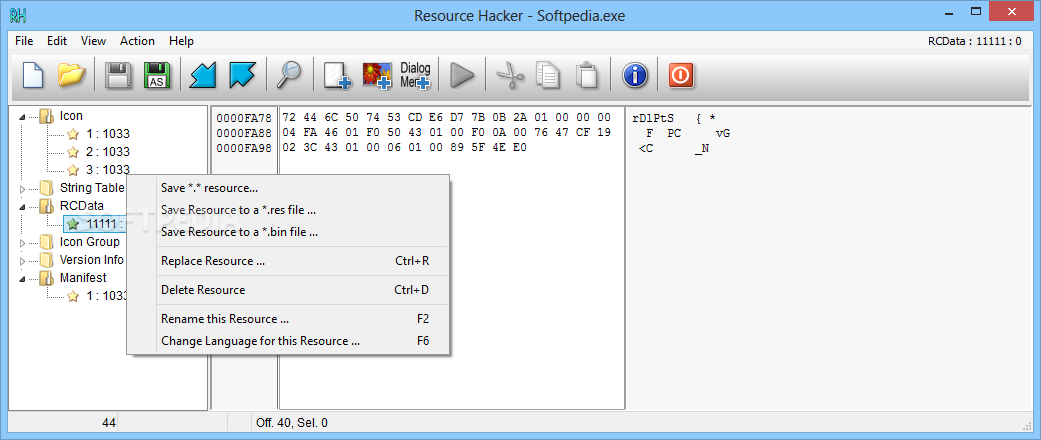
Resource Hacker is an application that provides basically the easiest method to get past the .exe or .dll extension in order to see the resources inside a certain file, providing you even more than that.
Resource Hacker has a very simple and clean interface and although it’s not exactly the kind of application that should be used by beginners, it does all things a lot easier.
With a classy look that reminds us of older Windows versions, this app provides all the tools you need when opening executables or DLL files through a single click.
Thus you can save resources as a binary file or with a .res extensions, you can replace icons, cursors and bitmaps, change texts and add new resources in a second.
Right clicking on a file components opens a new options menu, giving you the power to save, replace, rename or delete resources, but also to change languages on the go.
Resource Hacker is compatible with Win32 executable files (*.exe, *.dll, *.cpl, *.ocx) but also with Win32 resource files (*.res).
Download :
Resource Hacker 3.6.0.92